MCS–012, Question & Answer December 2023
1. (a) Convert the following decimal numbers to binary and hexadecimal : 6
(i) (28)10
(ii) (256)10
(iii) (42.25)10
### (i) \( (28)_{10} \)
\[
\begin{align*}
28 \div 2 &= 14 \quad \text{remainder: } 0 \\
14 \div 2 &= 7 \quad \text{remainder: } 0 \\
7 \div 2 &= 3 \quad \text{remainder: } 1 \\
3 \div 2 &= 1 \quad \text{remainder: } 1 \\
1 \div 2 &= 0 \quad \text{remainder: } 1 \\
\end{align*}
\]
Binary: \( (28)_{10} = (11100)_2 \)
#### Conversion to Hexadecimal:
\[
\begin{align*}
28 \div 16 &= 1 \quad \text{remainder: } 12 \quad (12 = C) \\
1 \div 16 &= 0 \quad \text{remainder: } 1 \\
\end{align*}
\]
Hexadecimal: \( (28)_{10} = (1C)_{16} \)
### (ii) \( (256)_{10} \)
#### Conversion to Binary:
\[
\begin{align*}
256 \div 2 &= 128 \quad \text{remainder: } 0 \\
128 \div 2 &= 64 \quad \text{remainder: } 0 \\
64 \div 2 &= 32 \quad \text{remainder: } 0 \\
32 \div 2 &= 16 \quad \text{remainder: } 0 \\
16 \div 2 &= 8 \quad \text{remainder: } 0 \\
8 \div 2 &= 4 \quad \text{remainder: } 0 \\
4 \div 2 &= 2 \quad \text{remainder: } 0 \\
2 \div 2 &= 1 \quad \text{remainder: } 0 \\
1 \div 2 &= 0 \quad \text{remainder: } 1 \\
\end{align*}
\]
Binary: \( (256)_{10} = (100000000)_2 \)
#### Conversion to Hexadecimal:
\[
\begin{align*}
256 \div 16 &= 16 \quad \text{remainder: } 0 \\
16 \div 16 &= 1 \quad \text{remainder: } 0 \\
1 \div 16 &= 0 \quad \text{remainder: } 1 \\
\end{align*}
\]
Hexadecimal: \( (256)_{10} = (100)_{16} \)
### (iii) \( (42.25)_{10} \)
#### Conversion to Binary:
**Integer part:**
\[
\begin{align*}
42 \div 2 &= 21 \quad \text{remainder: } 0 \\
21 \div 2 &= 10 \quad \text{remainder: } 1 \\
10 \div 2 &= 5 \quad \text{remainder: } 0 \\
5 \div 2 &= 2 \quad \text{remainder: } 1 \\
2 \div 2 &= 1 \quad \text{remainder: } 0 \\
1 \div 2 &= 0 \quad \text{remainder: } 1 \\
\end{align*}
\]
Integer part in binary: \( 101010_2 \)
**Fractional part:**
1. Multiply the fractional part by 2 and record the integer part.
2. Repeat for the fractional part until it becomes 0.
\[
\begin{align*}
0.25 \times 2 &= 0.5 \quad \text{integer part: } 0 \\
0.5 \times 2 &= 1.0 \quad \text{integer part: } 1 \\
\end{align*}
\]
Fractional part in binary: \( .01_2 \)
Binary: \( (42.25)_{10} = (101010.01)_2 \)
#### Conversion to Hexadecimal:
**Integer part:**
\[
\begin{align*}
42 \div 16 &= 2 \quad \text{remainder: } 10 \quad (10 = A) \\
2 \div 16 &= 0 \quad \text{remainder: } 2 \\
\end{align*}
\]
Integer part in hexadecimal: \( 2A_{16} \)
**Fractional part:**
1. Multiply the fractional part by 16 and record the integer part.
2. Repeat for the fractional part until it becomes 0.
\[
\begin{align*}
0.25 \times 16 &= 4.0 \quad \text{integer part: } 4 \\
\end{align*}
\]
Fractional part in hexadecimal: \( .4_{16} \)
Hexadecimal: \( (42.25)_{10} = (2A.4)_{16} \)
### Summary
- \( (28)_{10} = (11100)_2 = (1C)_{16} \)
- \( (256)_{10} = (100000000)_2 = (100)_{16} \)
- \( (42.25)_{10} = (101010.01)_2 = (2A.4)_{16} \)
(b) What is half-adder ? Make the truth table and logic diagram of a half-adder.
A half-adder is a basic digital circuit used for adding two single-bit binary numbers. It produces two outputs: the sum (S) and the carry (C). The sum represents the addition result, and the carry represents the overflow that is carried to the next higher bit in multi-bit addition.
Truth Table
Logic Diagram
The half-adder uses two logic gates:
1. **XOR Gate** for the sum (S).
2. **AND Gate** for the carry (C).
The logic diagram is as follows:
- - **Inputs:** A and B
- - **Sum (S):** \( A \oplus B \) (XOR gate)
- - **Carry (C):** \( A \cdot B \) (AND gate)
- Purpose: Holds the base address of the code segment, where the executable instructions are stored.
- Example: If CS=0x1000 and the instruction pointer (IP) is 0x0005, the CPU fetches the instruction from address 0x10005 (CS:IP).
- Purpose: Contains the base address of the data segment, where variables and data structures are stored.
- Example: If DS=0x2000 and an instruction like MOV AX, [1234H] is executed, it fetches data from address 0x21234.
- Purpose: Holds the base address of the stack segment, used for stack operations like push and pop.
- Example: If SS=0x3000 and the stack pointer (SP) is 0xFFFE, a PUSH AX operation stores the value of AX at address 0x3FFFE, and SP is decremented.
- Purpose: Used as an additional data segment, often for string operations.
- Example: If ES=0x4000, and MOVS instruction is executed to move a string from DS:SI to ES:DI, it transfers data starting from address 0x40000.
- Load the character into the DL register.
- Set AH to 02h (function number for displaying a character).
- Execute INT 21h.
- The .model small directive sets up a small memory model where both code and data are in the same segment.
- The .stack 100h directive allocates 256 bytes for the stack.
- The .data section is where the variables mem_loc1 and mem_loc2 are declared with initial values.
- mov ax, @data and mov ds, ax initialize the data segment register DS to point to the data segment.
- mov si, offset mem_loc1 loads the offset of mem_loc1 into SI.
- mov al, [si] loads the byte value at mem_loc1 into AL.
- mov di, offset mem_loc2 loads the offset of mem_loc2 into DI.
- mov bl, [di] loads the byte value at mem_loc2 into BL.
- mov [si], bl stores the value from BL into the memory location mem_loc1.
- mov [di], al stores the value from AL into the memory location mem_loc2.
- mov ah, 4Ch and int 21h terminate the program and return control to the operating system.







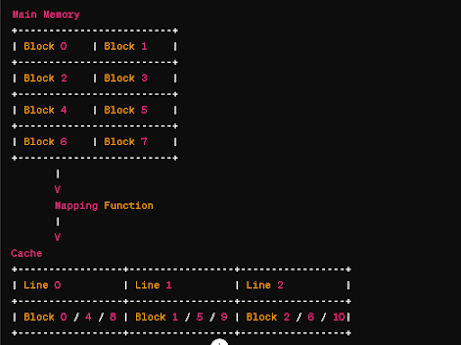













_page-0097.jpg)
Comments
Post a Comment